Application & Infrastructure Scanning
A leading security scanning platform that automates the discovery of security flaws within your websites, applications, network, and cloud infrastructure.
Secure development
life cycle
Assessments can be conducted throughout the application life cycle from development to production. Integrates with common development tools.
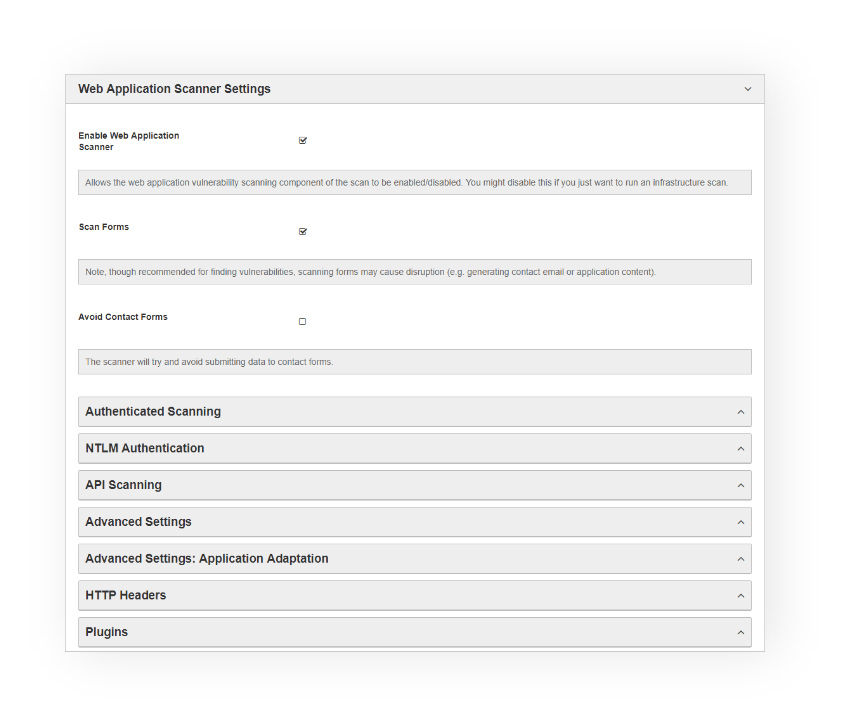
Intuitive & flexible
configurations
Scans can be launched in seconds using pre-defined scan profiles. Each finding within the report includes a detailed narrative and easy to understand remediation advice.
Unlimited testing and
unlimited users
All licences provide unlimited users and unlimited scanning 24 hours a day 365 days a year.
ORGANISATIONS WHO CURRENTLY BENEFIT FROM THE PLATFORM
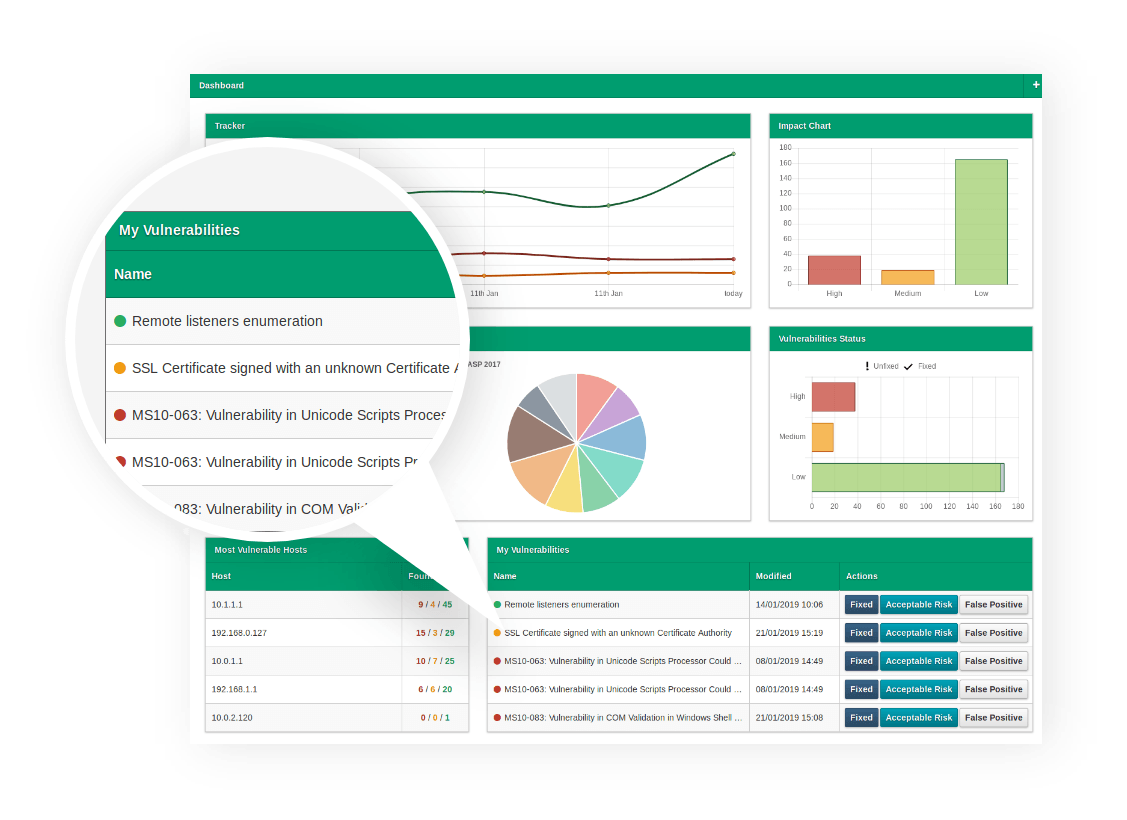
Automatic vulnerability management
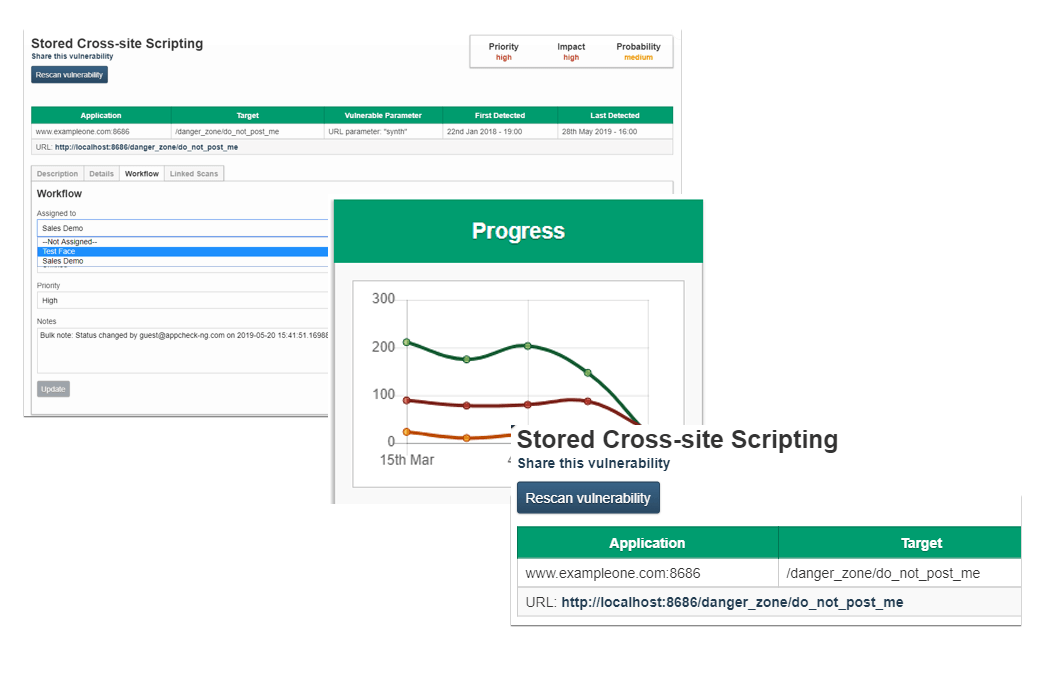
A built-in workflow management system that allows individual findings to be assigned to a member of the team. Remediation progress can then be tracked visually through the main dashboard. A rescan against each vulnerability can be performed with a single click to test the effectiveness of applied fixes. Scans can also be configured to automatically rescan when a vulnerability is marked as fixed.
DID YOU KNOW?
It can be difficult from an internal resource and cost point of view to keep with an ever changing threat landscape. Our tool and managed penetration testing service mitigates this.
KEY TECHNICAL FEATURES
Zero day detection
Detect security flaws by adopting a first principles methodology rather than firing checks from a known vulnerability database. This approach successfully identifies security flaws within that are previously unknown and undisclosed.
Browser-based crawler
a browser-based crawler that combines application modelling techniques and subtle heuristical cues to automatically discover the complete attack surface of any given application in the shortest time possible.
Easy to use scripting language
An easy to use scripting language named GoScript which can be used to navigate and scan complex workflows and single page applications.
Seamless API integration
A JSON based API is available as standard to provide integration with development tools and other systems. The API can be used to drive scans and retrieve results as part of your continuous integration and development processes.
Safe exploitation
Many of the scanning modules include an option to safely exploit vulnerabilities so that real business impact can be demonstrated to all stake holders from board level to the development team.
OWASP Top 10
Web application scanning covers all known vulnerability classes including all of the OWASP top 10. Easily view and manage all your known OWASP top 10 vulnerabilities in customisable dashboards, scans and reports.
DID YOU KNOW?
Only 52% of large businesses and 23% of high-income charities carry out Penetration Testing
Frequently Asked Questions
YOU MAY ALSO LIKE...
A penetration test ultimately seeks to answer the question “How effective is my organisation’s security controls against a skilled human hacker?” while determining the security posture of your organisation's network infrastructure and identifying any potential risks.
Birthday Sparks
There are many different penetration testing methods that can be carried out against your business. They all have their own unique benefits and should be carried out annually, as a minimum requirement, to ensure continuing business compliance
A web application penetration test aims to identify security issues resulting from vulnerabilities in the design, coding and publishing of software or a website.
SPEAK WITH A CYBER EXPERT TODAY
Fill in the form or call us on 0333 305 0605 and one of our Cyber Security experts will be happy to assist you